Created: 21/10/2024 22:45
Last Updated: 23/10/2024 14:16
In the afternoon, network monitoring systems detected anomalous traffic patterns originating from a critical transaction processing server. Initial signs suggest a potential security breach. You have been provided with a forensic image of the affected system and tasked with conducting a thorough investigation to determine the scope of the incident.
Start Investigation
What is the name of the key file the intruder downloaded to elevate their privileges after gaining unauthorized access?
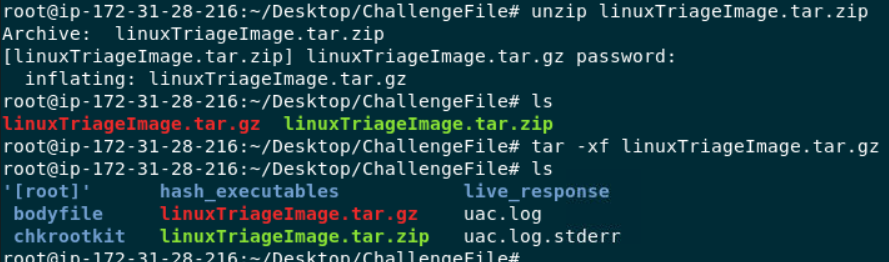 Lets see what we got first, this challenge provided us with artifacts collected by Unix-like Artifacts Collector (uac) which will collect various files from disk image and also running various command during execution time to collect live forensic environment artifacts.
Lets see what we got first, this challenge provided us with artifacts collected by Unix-like Artifacts Collector (uac) which will collect various files from disk image and also running various command during execution time to collect live forensic environment artifacts.
So knowing what we have, take a look at the scenerio again which telling us there is some traffic anomaly and based on the challenge name, it indicated that an attacker exploited kernel to gain root shell and successfully exfiltrated data so knowing this I started by taking a look at process when UAC was executed. (under live_response -> process)
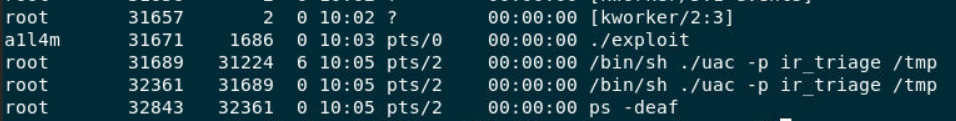
Pick any of ps like command output then I found ./exploit (ProcessID 31671) was executed by a1l4m user so this should be the one we are after!
Answer
exploit
When was the file used for privilege escalation first submitted on Virus Total?
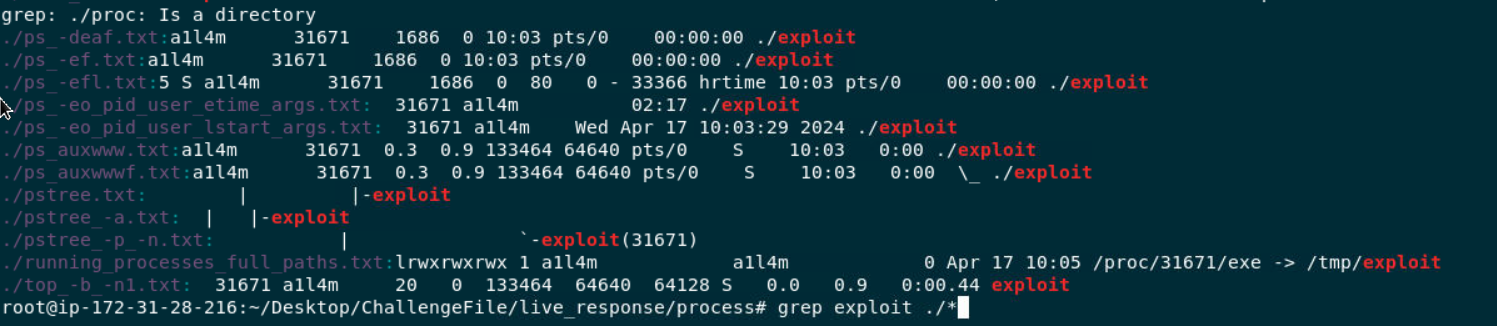 Lets find out where this binary was executed from, which we can see that it was executed from
Lets find out where this binary was executed from, which we can see that it was executed from /tmp directory which make it more suspicious.
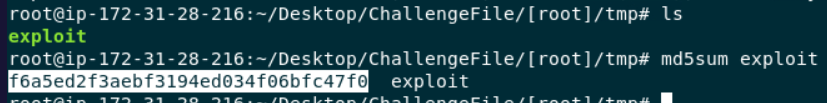 Now we already know where it resides then we can go to
Now we already know where it resides then we can go to /[root]/tmp to get this file and calculate filehash
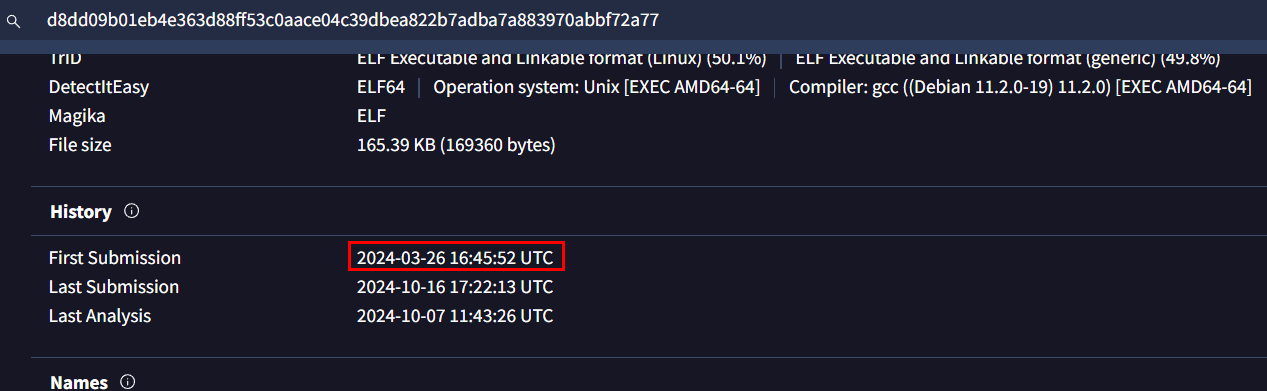
Search this hash on VirusTotal and Go to "History" section under "Details" tab which we can see first submission time of this binary
Answer
2024-03-26 16:45:52 UTC
What is the Process ID (PID) of the operation launched by the attacker?
Answer
31671
What username was the malicious process running under?
Answer
a1l4m
What is the Parent Process ID (PPID) associated with the malicious process?
Answer
1686
What are the operating system and its version on the compromised server?
Answer Format:version-os
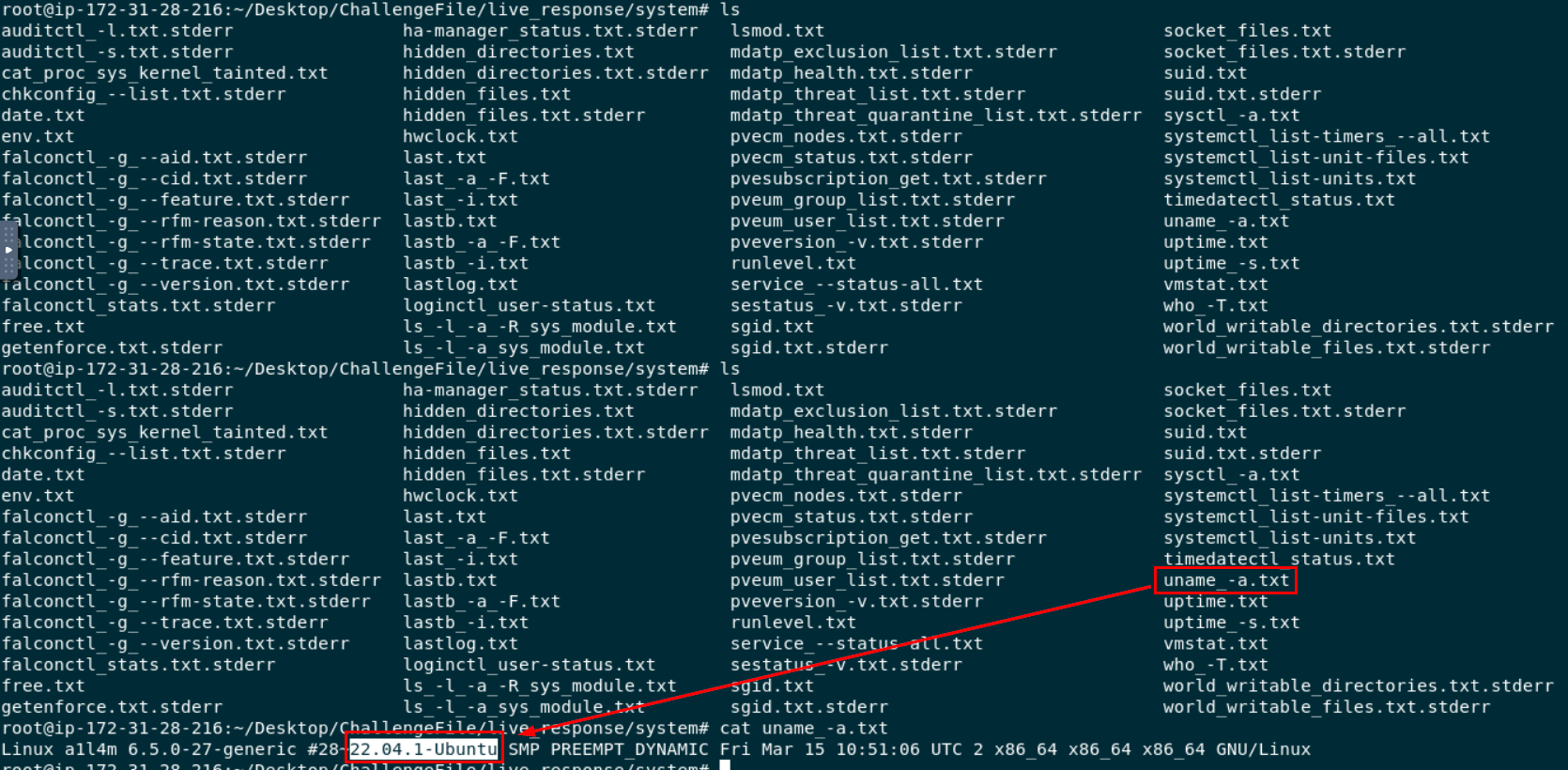 For this one, we have to go to
For this one, we have to go to /live_response/system that stored result of various commands specific to system and configuration then we can print out content of uname command here which contains OS and kernel version of this compromised system
Answer
22.04.1-Ubuntu
What is the kernel version of the compromised system?
Answer
6.5.0-27-generic
What is the most recent CVE number associated with the vulnerabilities exploited in this attack?
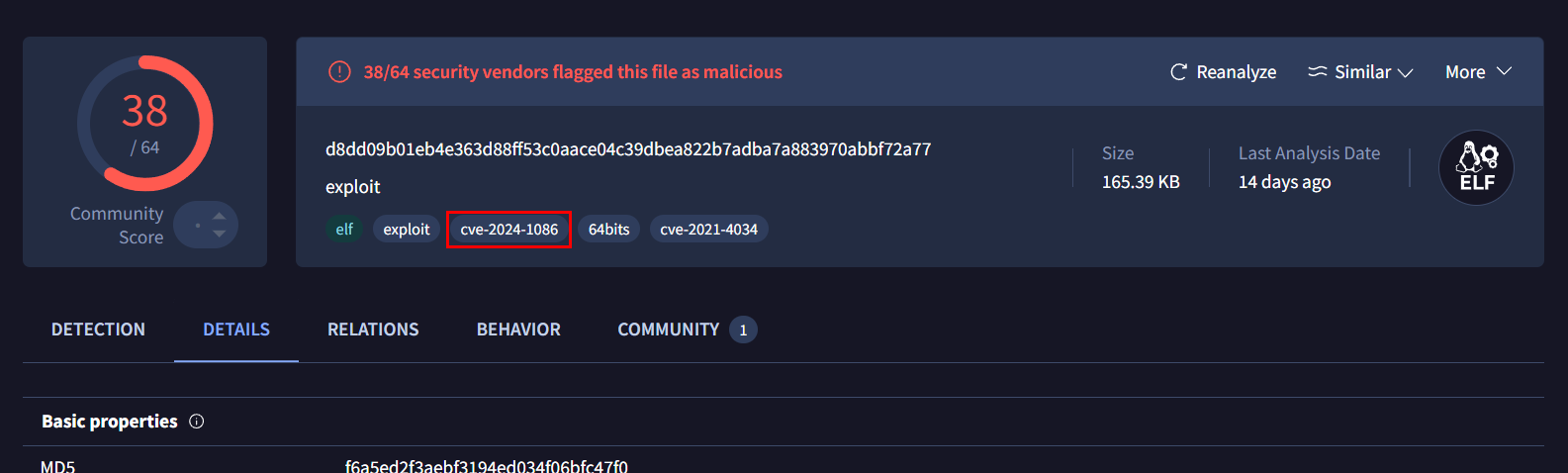 Go back to VirusTotal then we will have 2 candidates CVE but the most recent one (which found in this year) is CVE-2024-1086 which affected Linux kernal from 3.15 to 6.1.76, 6.2 to 6.6.15 and 6.7 to 6.7.3 that means this compromised system is vulnerable to this exploit!
Go back to VirusTotal then we will have 2 candidates CVE but the most recent one (which found in this year) is CVE-2024-1086 which affected Linux kernal from 3.15 to 6.1.76, 6.2 to 6.6.15 and 6.7 to 6.7.3 that means this compromised system is vulnerable to this exploit!
Answer
cve-2024-1086
Summary
On this challenge, we investigated linux kernel exploit from artifacts collected by UAC which collected various files and output of various commands during artifacts acquisition that helped us pin point which process is the most suspicious one and where it located on disk image of compromised system!

 Lets see what we got first, this challenge provided us with artifacts collected by Unix-like Artifacts Collector (uac) which will collect various files from disk image and also running various command during execution time to collect live forensic environment artifacts.
Lets see what we got first, this challenge provided us with artifacts collected by Unix-like Artifacts Collector (uac) which will collect various files from disk image and also running various command during execution time to collect live forensic environment artifacts.
 Lets find out where this binary was executed from, which we can see that it was executed from
Lets find out where this binary was executed from, which we can see that it was executed from  Now we already know where it resides then we can go to
Now we already know where it resides then we can go to 
 For this one, we have to go to
For this one, we have to go to  Go back to VirusTotal then we will have 2 candidates CVE but the most recent one (which found in this year) is
Go back to VirusTotal then we will have 2 candidates CVE but the most recent one (which found in this year) is